61 | Add to Reading ListSource URL: www.mychallenge.abarthworld.comLanguage: English - Date: 2013-03-26 12:27:39
|
|---|
62 | Add to Reading ListSource URL: cocoa.ethz.chLanguage: English - Date: 2013-07-17 07:17:50
|
|---|
63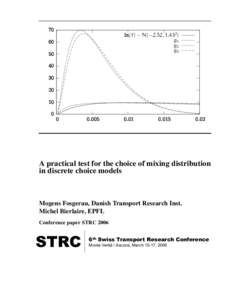 | Add to Reading ListSource URL: www.strc.chLanguage: English - Date: 2008-11-28 01:59:20
|
|---|
64 | Add to Reading ListSource URL: www.securitywarriorconsulting.comLanguage: English - Date: 2010-03-23 02:04:48
|
|---|
65 | Add to Reading ListSource URL: www.proficiencylabs.comLanguage: English - Date: 2013-04-16 18:59:08
|
|---|
66 | Add to Reading ListSource URL: irtf.orgLanguage: English - Date: 2016-01-05 05:04:04
|
|---|
67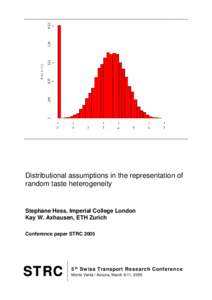 | Add to Reading ListSource URL: www.strc.chLanguage: English - Date: 2008-12-12 11:45:19
|
|---|
68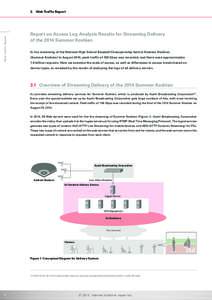 | Add to Reading ListSource URL: www.iij.ad.jpLanguage: English - Date: 2015-12-27 21:34:14
|
|---|
69 | Add to Reading ListSource URL: www.tyronegrandison.orgLanguage: English - Date: 2013-04-16 18:57:15
|
|---|
70 | Add to Reading ListSource URL: manyasleeper.comLanguage: English - Date: 2015-07-08 14:57:23
|
|---|